Unified Cyber Defense Platform
We don’t just monitor your infrastructure. Threat intelligence, compliance, training, and immediate incident response.
Smart Access Monitoring
Detect suspicious patterns and protect your infrastructure with real-time authentication analysis.
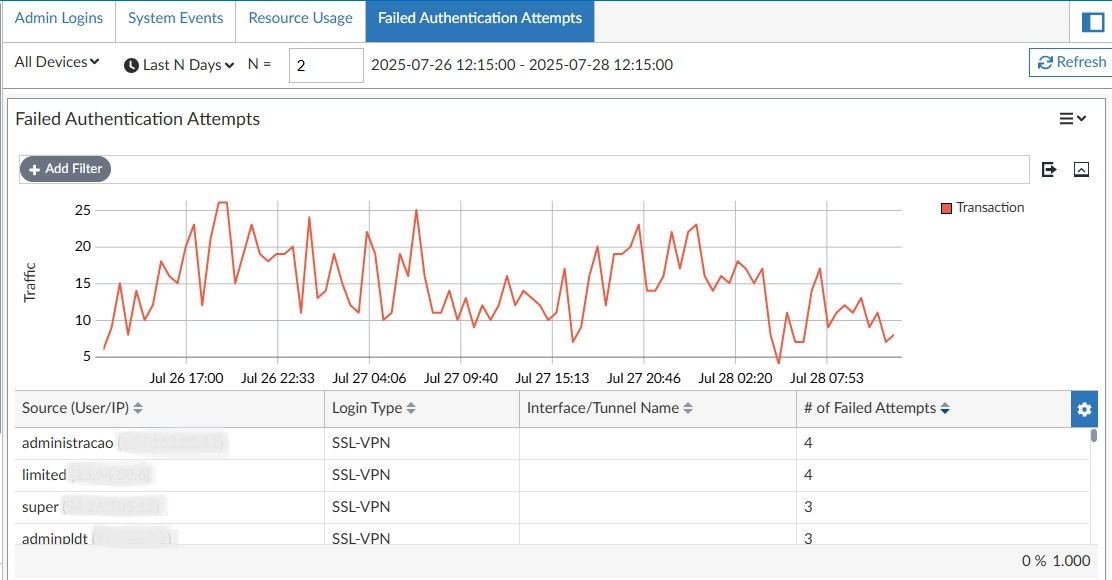
Authentication Dashboard
Real-time view of authentication events, geographic anomalies, and risk scores.
Access Monitoring
Analyze access patterns and detect suspicious behavior in real time.
Geographic Analysis
Identify logins from unusual locations and block suspicious attempts.
Anomaly Detection
Detect impossible travel and brute force attempts with ML-based signals.
Threat Detection and Analysis
Identify, classify, and prioritize threats with AI and advanced real-time forensics.
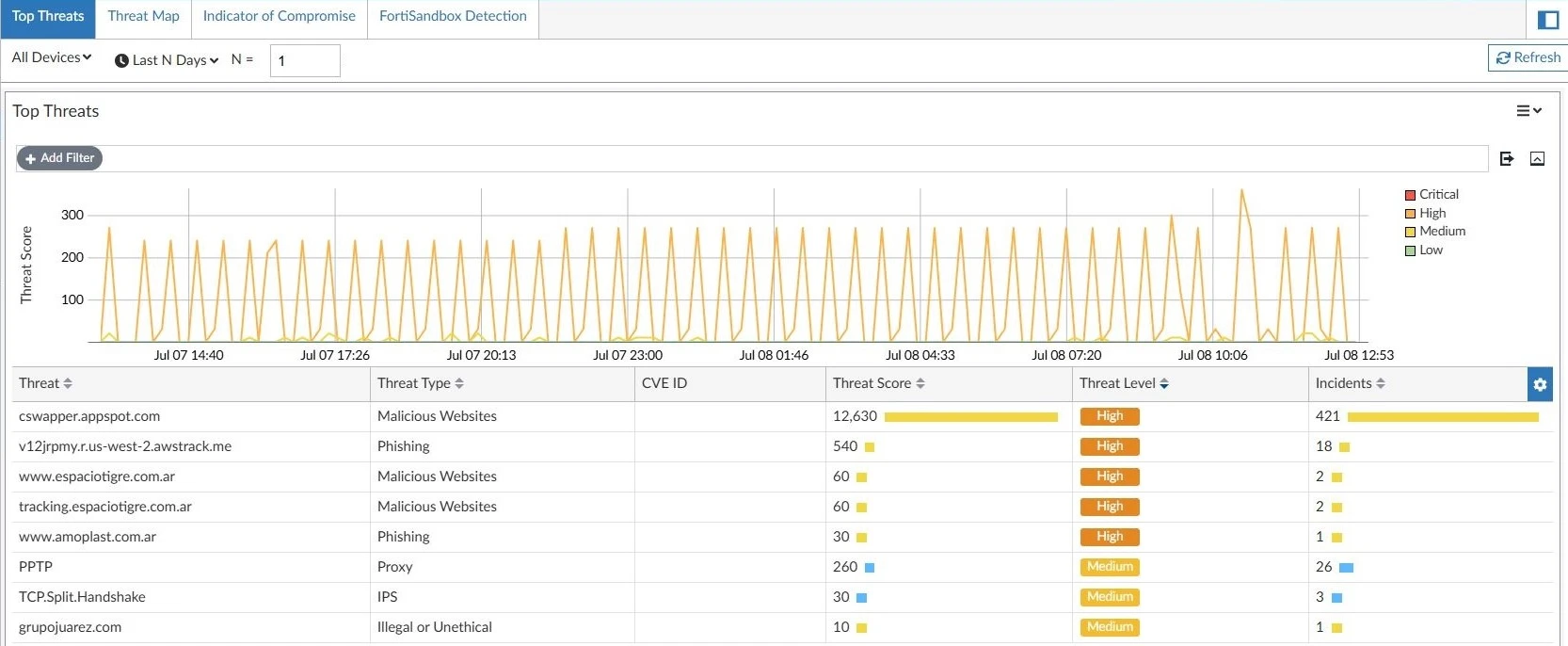
Threat View
Critical threats prioritized by impact, frequency, and kill chain stage.
Threat Ranking
Visualize the most critical threats prioritized by impact and frequency.
Attack Vector Analysis
Identify malicious patterns and compromise paths used by attackers.
Indicators of Compromise (IOCs)
Detect malicious IPs, suspicious domains, and known malware signatures.
System Resource Monitoring
Ensure availability and optimization by tracking critical resource usage.
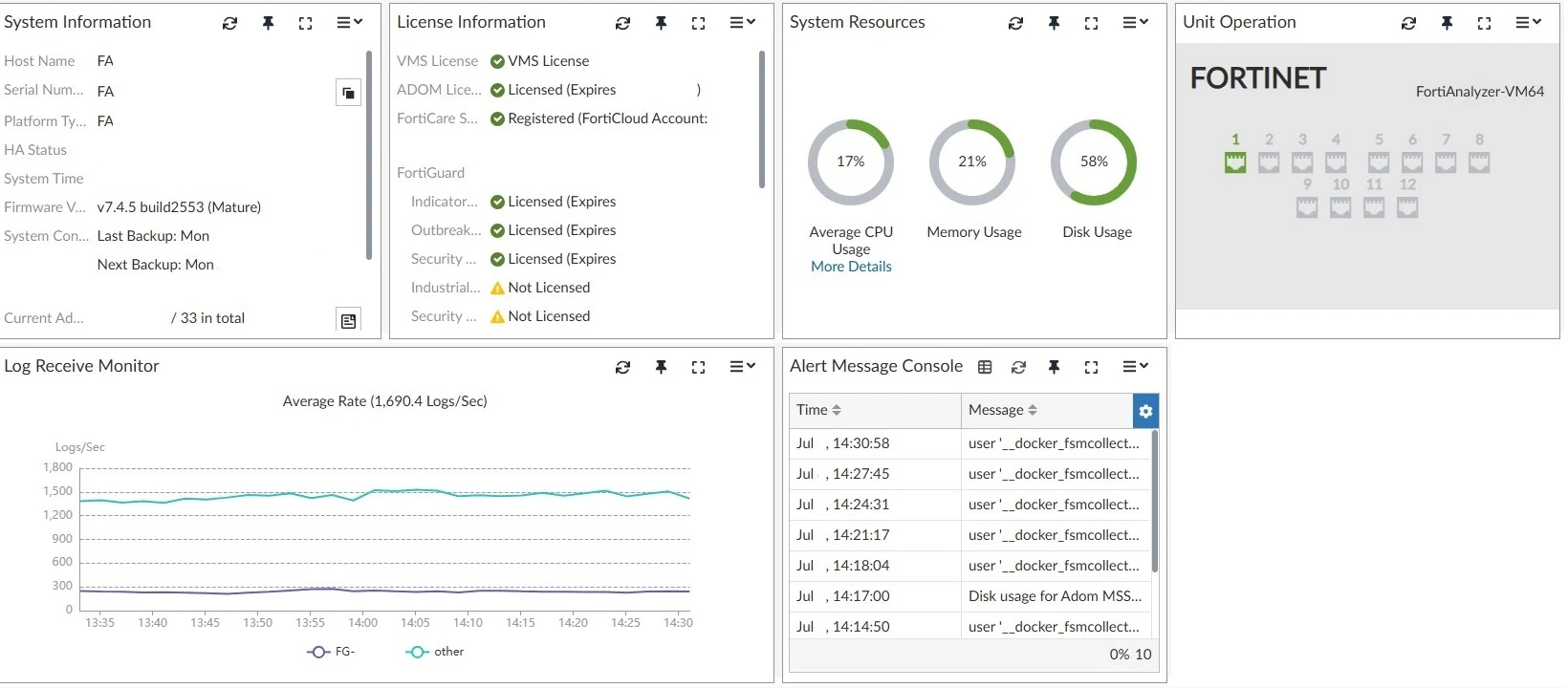
Resource Monitoring
CPU, memory, storage, and network throughput in a unified view.
CPU Performance
Monitor processor load and identify activity spikes.
Storage Management
Track disk usage, forecast growth, and automate retention.
Network Throughput
Measure bandwidth for log ingestion and data replication.
Centralized Event Management
Centralize, correlate, and analyze events with advanced search and forensics.
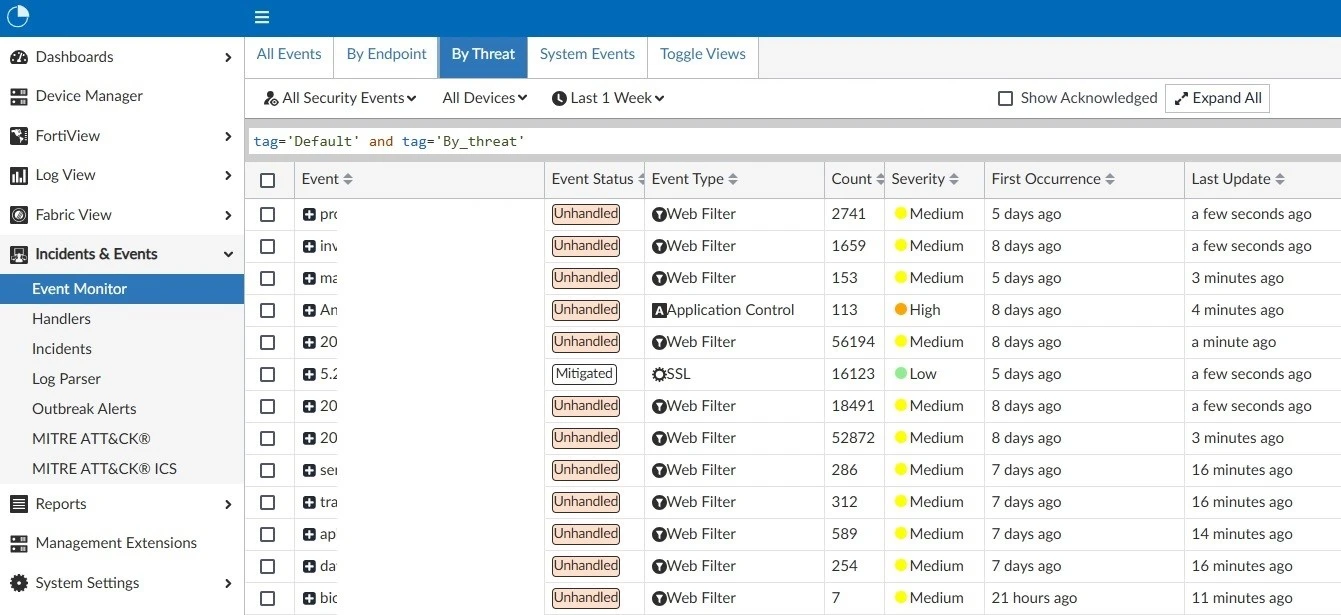
Event Explorer
Centralized logs with advanced search, filters, and correlations.
Log Centralization
Unify events from firewalls, IDS/IPS, servers, and applications.
Advanced Search & Filters
Find specific events among millions of records.
Incident Timeline
Reconstruct the attack chain with a chronological view.

